Written by Chip Andrews from SQLSecurity.com, SQLRecon performs both active and passive scans of your network in order to identify all of the Microsoft SQL Server (or MSDE) installations in your enterprise.
Due to the proliferation of personal firewalls, inconsistent network library configurations, and multiple-instance support, SQL Server installations are becoming increasingly difficult to discover, assess, and maintain. SQLRecon is designed to remedy this problem by combining all known means of MS-SQL/MSDE discovery into a single tool which can be used to ferret-out servers you never knew existed on your network so you can properly secure them.
Features
- Multi-threaded scanning engine
- 6 Active scanning techniques
- 2 Stealth scanning techniques
- IP Range and List scanning
- Export results as XML or text file
- Export IP list for use in future scans (i.e. Passive to Active)
- ICMP check to increase scan speed
- Debug mode to allow for greater scan visibility
- Allows alternate credentials
- Custom source port for UDP packets for firewall evasion
End-User License Agreement
Please read this entire agreement, scroll down to the bottom, and indicate your acceptance of this EULA by clicking the download link.
1. ACCEPTANCE OF TERMS
Read these Special Ops Security, Inc. (“Special Ops Security”) Terms of Use (“Terms”) carefully before you (“You”) accept these Terms by downloading the software. If You do not agree to all of these Terms, do not download the software. The Terms are entered into by and between Special Ops Security and You. Special Ops Security provides the Tools to You strictly subject to the Terms.
2. RESTRICTIONS ON USE
You may not modify, reverse engineer, make derivative works of, distribute, transmit or sell any of the Tools without the express written consent of Special Ops Security. The Tools may not be used by You or any other party for any purpose that violates any local, state, federal or foreign law. You understand that breaking into any network or computer system not owned by You may be illegal.
3. NO EXPRESS OR IMPLIED WARRANTY
THE TOOLS ARE PROVIDED TO YOU “AS IS.” SPECIAL OPS SECURITY MAKES NO WARRANTIES OR REPRESENTATIONS, EXPRESS OR IMPLIED, ABOUT THE EFFECTIVENESS, COMPLETENESS OR FITNESS OF THE TOOLS, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
4. LIMITATION OF LIABILITY
YOU AGREE THAT SPECIAL OPS SECURITY WILL NOT BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, CONSEQUENTIAL OR PUNITIVE DAMAGES ARISING OUT OF YOUR USE OF, OR INABILITY TO USE, THE TOOLS, INCLUDING WITHOUT LIMITATION ANY DAMAGE TO, OR VIRUSES OR “TROJAN HORSES” THAT MAY INFECT OR INVADE, YOUR COMPUTER EQUIPMENT OR OTHER PROPERTY, EVEN IF SPECIAL OPS SECURITY IS EXPRESSLY ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. YOU AGREE TO HOLD SPECIAL OPS SECURITY HARMLESS FROM, AND YOU COVENANT NOT TO SUE SPECIAL OPS SECURITY FOR, ANY CLAIMS BASED OR YOUR USE OF, OR YOUR INABILITY TO USE, THE TOOLS.
5. INDEMNIFICATION
You agree to indemnify and hold Special Ops Security and its subsidiaries, affiliates, officers, agents, and employees harmless from any claim or demand, including attorney’s fees, made by any third party due to or arising out of Your use of the Tools, breach of the Terms, or violation of the rights of another.
6. INTELLECTUAL PROPERTY RIGHTS
The Tools and all names, marks, brands, logos, designs, trade dress and other designations Special Ops Security uses in connection with the Tools are proprietary to Special Ops Security and are protected by applicable intellectual property laws, including, but not limited to copyrights and trademarks. Accordingly, You may not modify, reverse engineer, make derivative works of, distribute, transmit or sell any of the Tools, nor may You remove or alter any of Special Ops Security’s trademarks from the Tools or co-brand any of the Tools, without the express written consent of Special Ops Security.
7. VENUE
Nevada law and controlling United States federal law govern any action related to the Terms. No choice of law rules of any jurisdiction apply. You and Special Ops Security agree to submit to the personal and exclusive jurisdiction of the Nevada state court located in Las Vegas, Nevada and the United States District Court for the Central District of Nevada.
Special Ops Security controls and operates this website from various locations in the United States of America and makes no representation that these Tools are appropriate or available for use in other locations. If you use this website from locations outside the United States of America, You are responsible for compliance with applicable local laws, including, but not limited to, the export and import regulations of other countries.
8. MISCELLANEOUS
The Terms constitute the entire agreement between You and Special Ops Security and govern Your use of the Tools, superseding any prior agreements between You and Special Ops Security (including, but not limited to, prior versions of the Terms). These Terms and this website could include inaccuracies or typographical errors. Special Ops Security may make improvements and/or changes to the Terms or the website at any time without notice. The failure of Special Ops Security to enforce or exercise any right or provision of the Terms does not constitute a waiver of such right or provision. In the event any provision of this Agreement is held to be unenforceable in any respect, such unenforceability shall not affect any other provision of this Agreement, provided that the expected economic benefits of this Agreement are not denied to either party.
Accept EULA and download
Documentation
This documentation is for version 1.0 (March 2005).
INSTRUCTIONS
SQLRecon was designed to be simple to configure and operate. Simply execute the SQLRecon.exe file downloaded from the website. After the application loads, the basic operation is as follows.
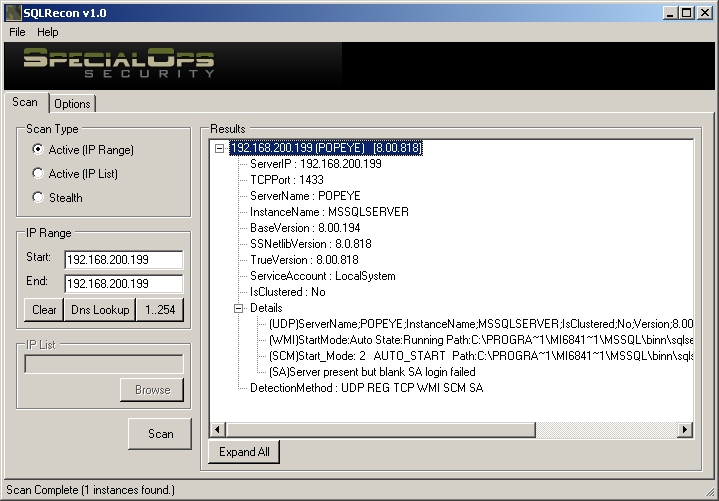
CHOOSE A SCAN TYPE
Based on your scan type enter the scan criteria (IP address range or list file) Click the Scan button to begin the scan.
SCAN TYPES
SQLRecon has three scan types:
- Active (IP Range) – A range of IP addresses is actively scanned one by one until all hosts have been assessed for SQL Server instances. (The term active implies that packets are directed precisely at those hosts and the scan will be observed if any network or host-based IDS systems are active.)
- Active (IP List) – An imported list on IP addresses is actively scanned for SQL Server instances. This is useful in situations where you need to be more selective about which machines are being checked. This scan is also useful for a deeper scan of machines that may have been identified in a Stealth scan.
- Stealth – This scan sends no packets directly to the hosts being discovered. Instead, this mode uses techniques to discovery SQL Server instances that involve contacting third party services that are already aggregating this information.
As the scan progresses, you will see the results appear in the right pane. The results will appear in treeview form in collapsed mode. You can expand each node for more information by clicking the plus (+) symbol by each entry. By clicking the “Expand All” button, you can also expand the entire tree. Once expanded, the button will change to “Collapse All” and have the opposite effect.
FILE EXPORT
Once your scan is complete, you have the option of saving the complete results or simply a list of IP addresses. In order to access this feature, simply click on the File menu at the top of the screen.
FILE -> SAVE -> FULL REPORT
This option will export all of the data from the scan in either an XML or comma-delimited text file that you designate.
FILE -> SAVE -> IP LIST
This option will export the discovered computers as a simple list of IP addresses. This is commonly done when you have performed a Stealth Scan and wish to do a more detailed, active scan of the machines discovered.
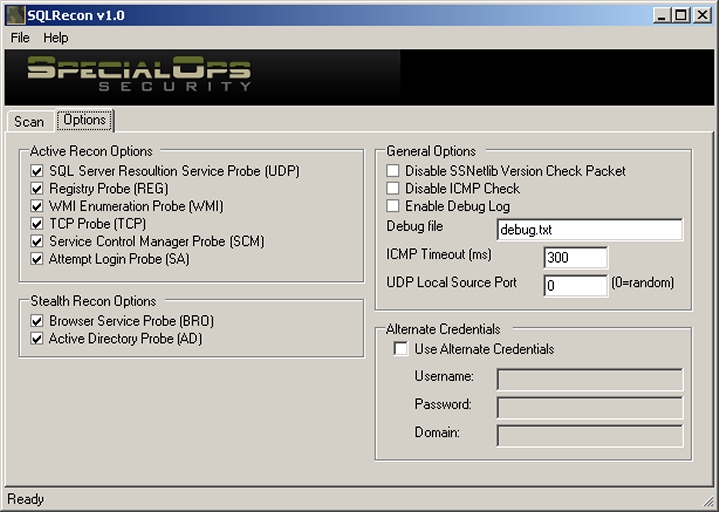
OPTIONS
The options tab will allow you to modify the operation of SQLRecon for your environment and help diagnose possible issues you may be having with discovery.
ACTIVE SCANNING PROBES
- UDP: Finds SQL Server 2000 instances by probing UDP 1434 (no auth required). This is the classic “SQLPing” probe.
- REG: Checks remote registry for SQL Server default instances (requires administrative privileges). This scan only works for default instances at the current time.
- WMI: Initiates a WMI query against the target machine (requires administrative privileges). While this scan can produce results from multiple instances, it will only work with administrative privileges in most environments.
- TCP: Port scan of TCP 1433/2433 (no auth required). 1433 is the default TCP port for SQL Server and MSDE. 2433 is the default port when the “Hide server” check box is selected in the TCP/IP properties of the Server Network Utility.
- SCM: Queries the service control manager of the remote machine (user privileges required). This scan is especially useful in scenarios where you may not have administrative privileges but still have domain user or equivalent.
- SA: Attempts to access the SQL Server instance with a blank password (no auth required). This qualifies as a scan type since they may be scenarios where all the other probes fail but an blatant attempt to access the system returns error messages signifying a server is present.
STEALTH SCANNING PROBES
- BRO: Checks the browser service for SQL Server registrations (no auth required). This scan will return minimal results but can return a nice list that you can export and then re-scan as an “active” type scan. This type of probe is also useful in cases where people may have a personal firewall enabled. Even if you can’t get more information, you’ll know the instances exist and you can audit them by more manual methods.
- AD: Queries Active Directory for registered SQL Servers (requires domain user privileges). This type of probe can return much more information than the BRO scan but at this time, Active Directory registration of SQL Server is still a voluntary process. That is, only persons who have opted to register their SQL Servers with Active Directory (using Enterprise Manager) will appear.
OTHER OPTIONS
- Disable SSNetlib Version Check Packet: Use this if you are not interested in the ssnetlib version or are wary of setting off alarms that look for that type of packet.
- Disable ICMP Check: Slows the scan but is useful if hosts may be blocking ICMP. If you select this option, the SQLRecon scan will slow significantly but may be the only way to get information from a host that is blocking ICMP.
- Enable Debug Log: Creates log file so you can monitor the reasons certain checks might be failing. If you wish to save your logs in a custom location, just use the input box called “Debug file” to specify the location you want.
- ICMP Timeout: Allows you to adjust the amount of time SQLRecon will wait for an ICMP reply before considering the remote machine to be inaccessible. You may want to increase this on dial-up or other slow links.
- UDP Source Port: Allows you to specify a custom source port for the UDP probe to allow it to pass through packet-filtering firewalls. For example, if the firewall only allows UDP 53 inbound, you could use this setting to get your request through the firewall and probe hosts behind it.
- Alternate Credentials: Provide alternate credentials here is you would like to perform the scans that require authentication using a different account.